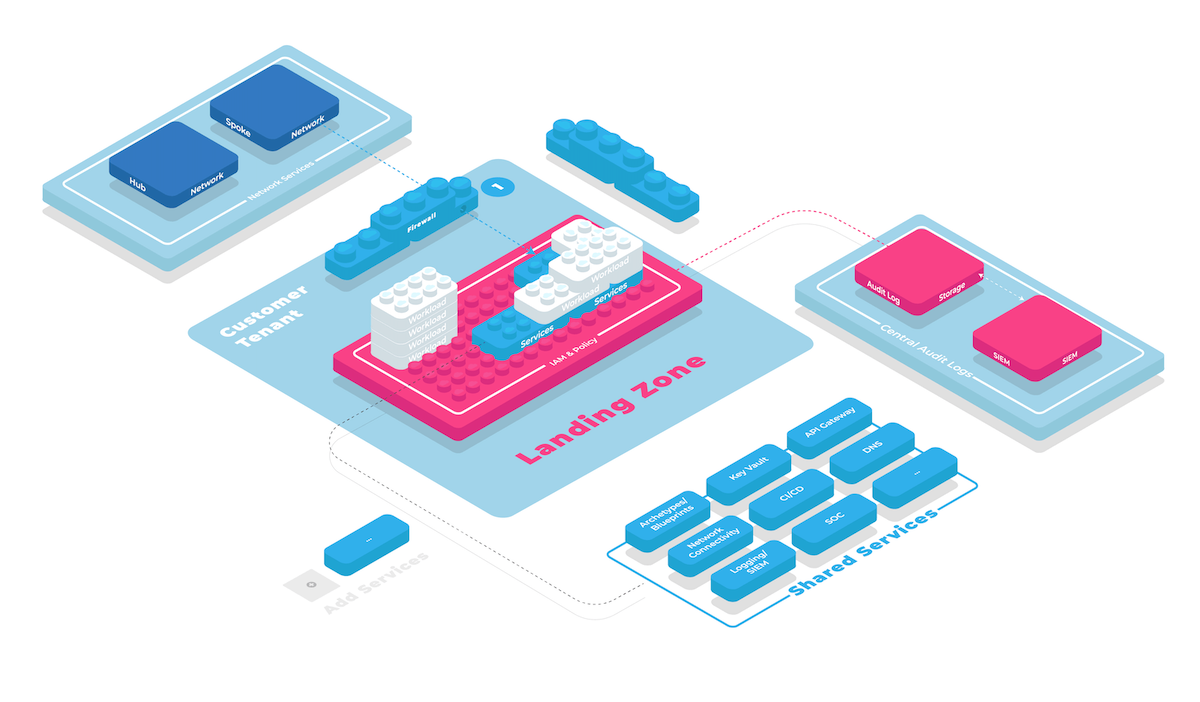
Logging
Source code & Installation
The source code of this kit module can be found here
Run the following command to install the kit module:
collie kit import azure/logging
Getting started with log analytics workspace
If you have not done so already, move an existing subscription into the management group hierarchy and check the policy assignment status in Azure Portal. We expect to see that the scope is compliant with the policy.
Here is how you interact with logs in your new workspace.
Open log analytics workspace in Azure portal. Choose the newly created workspace. Choose Workbooks → Activity Logs Insights. You will see stats about the Activity Logs streamed from the connected subscriptions to the log analytics workspace.
This assumes that in some Activity Log items has been generated in any of the
Alternatively, you can query logs. To do so, choose Logs in your workspace.
Here is a query that displays the last 50 Activity log events:
// Display top 50 Activity log events.
AzureActivity
| project TimeGenerated, SubscriptionId, ResourceGroup,ResourceProviderValue,OperationNameValue,CategoryValue,CorrelationId,ActivityStatusValue, ActivitySubstatusValue, Properties_d, Caller
| top 50 by TimeGenerated
2
3
4
Requirements
| Name | Version |
|---|---|
| terraform | >= 1.0 |
| azapi | ~> 1.12.1 |
| azuread | ~> 2.41.0 |
| azurerm | ~> 3.71.0 |
Modules
| Name | Source | Version |
|---|---|---|
| policy_law | github.com/meshcloud/collie-hub//kit/azure/util/azure-policies | ef06c8d43611dd3bf6eebdd7f472b95472f86b0b |
Resources
Inputs
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| cloudfoundation | this is the name of your cloud foundation | string | n/a | yes |
| cloudfoundation_deploy_principal_id | Principal ID authorized for deploying Cloud Foundation resources | string | n/a | yes |
| location | location of the resources created for logging | string | n/a | yes |
| log_retention_in_days | amount of time of log retention | number | 30 | no |
| logging_subscription_name | Name of your logging subscription | string | "logging" | no |
| parent_management_group_id | id of the parent management group that the logging subscription will be placed under | string | n/a | yes |
| scope | id of the management group that you want to collect activity logs from | string | n/a | yes |
| security_admin_group | the name of the cloud foundation security admin group | string | "cloudfoundation-security-admins" | no |
| security_auditor_group | the name of the cloud foundation security auditor group | string | "cloudfoundation-security-auditors" | no |
Outputs
| Name | Description |
|---|---|
| documentation_md | n/a |
| law_workspace_id | n/a |
| law_workspace_id_short | n/a |
| law_workspace_resource_id | n/a |
| logging_subscription | n/a |
| security_admins_azuread_group_id | n/a |
| security_auditors_azuread_group_id | n/a |