Azure Network
Source code & Installation
The source code of this kit module can be found here
Run the following command to install the kit module:
collie kit import azure/networking
1
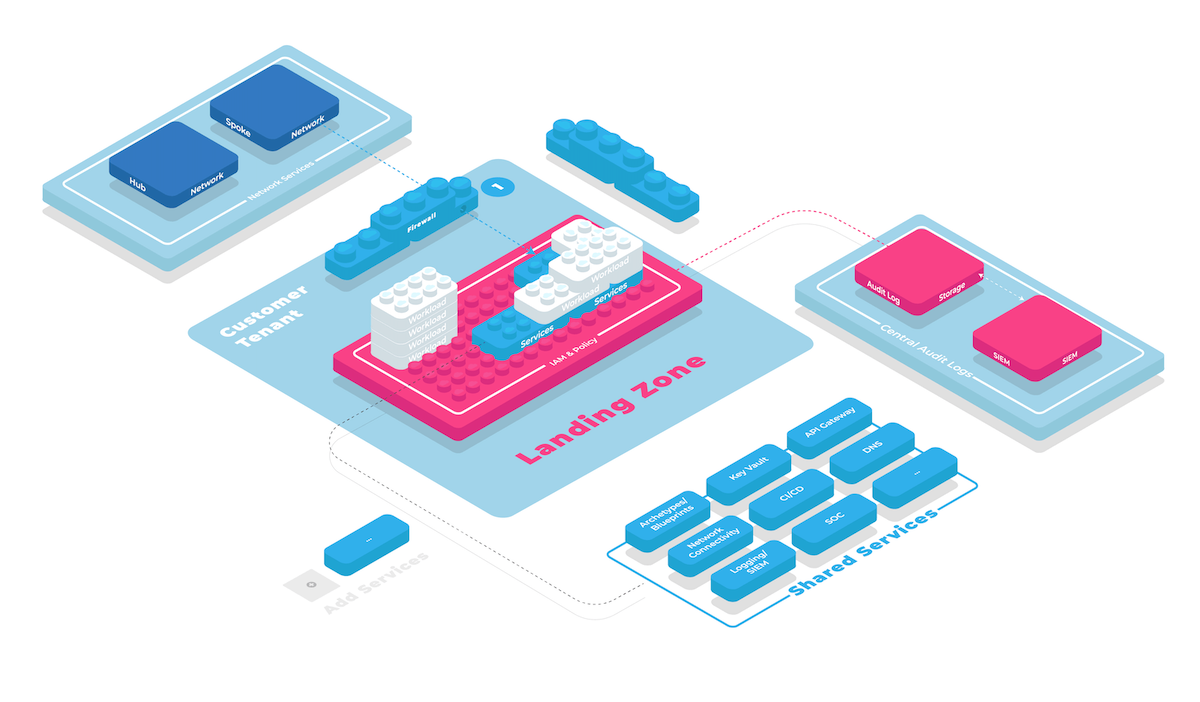
The Azure Network Kit defines the networking components within the Azure cloud environment. This infrastructure is designed to facilitate communication between various resources, whether they are within the same virtual network, on-premise, or on the internet.
Requirements
| Name | Version |
|---|---|
| terraform | >= 1.0 |
| azuread | ~> 2.41.0 |
| azurerm | ~> 3.85.0 |
Modules
No modules.
Resources
Inputs
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| address_space | List of address spaces for virtual networks | string | n/a | yes |
| cloudfoundation | Name of your cloud foundation | string | n/a | yes |
| cloudfoundation_deploy_principal_id | Principal ID authorized for deploying Cloud Foundation resources | string | n/a | yes |
| connectivity_scope | Identifier for the management group connectivity | string | n/a | yes |
| create_ddos_plan | Create a DDos protection plan and attach it to the virtual network. | bool | false | no |
| deploy_firewall | Toggle to deploy or bypass the firewall. | bool | false | no |
| diagnostics | Diagnostic settings for supporting resources. Refer to README.md for configuration details. | object({ | null | no |
| firewall_application_rules | List of application rules to apply to the firewall. | list(object({ | [] | no |
| firewall_nat_rules | List of NAT rules to apply to the firewall. | list(object({ | [] | no |
| firewall_network_rules | List of network rules to apply to the firewall. | list(object({ | [] | no |
| firewall_sku_tier | Specify the tier for the firewall, choosing from options like Basic or Standard, Premium. | string | "Basic" | no |
| firewall_zones | Collection of availability zones to distribute the Firewall across. | list(string) | null | no |
| hub_networking_deploy | Service Principal responsible for deploying the central hub networking | string | "cloudfoundation_hub_network_deploy_user" | no |
| hub_resource_group | Name of the central hub resource group | string | "hub-vnet-rg" | no |
| hub_subscription_name | Name of your hub subscription | string | "hub" | no |
| hub_vnet_name | Name of the central virtual network | string | "hub-vnet" | no |
| landingzone_scope | Identifier for the management group landinzone | string | n/a | yes |
| location | Region for resource deployment | string | n/a | yes |
| lz_networking_deploy | Service Principal responsible for deploying the landing zone networking | string | "cloudfoundation_lz_network_deploy_user" | no |
| management_nsg_rules | Network security rules to add to the management subnet. Refer to README for setup details. | list(any) | [] | no |
| netwatcher | Properties for creating network watcher. If set, it creates a Network Watcher resource using standard naming conventions. | object({ | null | no |
| network_admin_group | Name of the Cloud Foundation network administration group | string | "cloudfoundation-network-admins" | no |
| public_ip_names | List of public IP names connected to the firewall. At least one is required. | list(string) | [ | no |
| public_ip_prefix_length | Specifies the number of bits in the prefix. Value can be set between 24 (256 addresses) and 31 (2 addresses). | number | 30 | no |
| service_endpoints | Service endpoints to add to the firewall subnet. | list(string) | [ | no |
| threat_intel_mode | Operation mode for threat intelligence-based filtering. Possible values: Off, Alert, Deny, and "" (empty string). | string | "Off" | no |
Outputs
| Name | Description |
|---|---|
| documentation_md | n/a |
| firewall_name | Hub VNet firewall name |
| hub_location | Location of hub vnet |
| hub_rg | Hub Resource Group name |
| hub_subscription | Subscription of hub vnet |
| hub_vnet | Hub VNet name |
| network_admins_azuread_group_id | n/a |